Hackers exploit vulnerability stolen from NSA
The destructive power of ransomware was on full display today across nearly 100 countries worldwide, including the US, China Great Britain, Russia and Japan. Affected computers at countless organizations, including the UK’s National Health Service, displayed a message demanding $300 in Bitcoin to unlock stored data.
The tools used by hackers to commandeer the computers are believed to have been stolen from the US National Security Agency. The attacks caused serious business continuity issues at affected organizations and created havoc at some UK hospitals.
Experts believe the widespread incidents are linked, and some are describing today’s events as the “big one”—the massive ransomware event they believed was inevitable unless governments and companies across the globe took immediate proactive security measures.
Adam Kujuwa, a director at Malwarebytes, which discovered the original instance of today’s ransomware, said in a Wired article that today’s attacks are unprecedented.
“The spread is immense,” he said. “I’ve never seen anything before like this. This is nuts.”
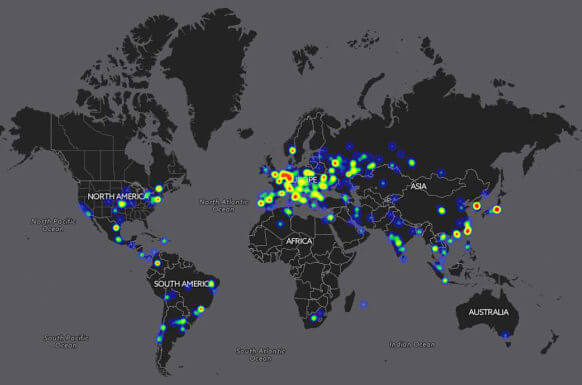
Illustration by Malwarehunterteam
Endpoint backup is an effective way to defend against ransomware.
“If you have a sound backup and recovery solution, you can recover files and resume normal operations instantly,” Vaultize’s Sameer Vitkar wrote in a recent blog post. “The extortion attempt can be greatly diminished if IT can recover infected files quickly. Having backup processes in place also protects your corporate data from instances of human error, accidents, hardware failures and any disaster that may otherwise result in complete or partial data loss. Basically, the investment in an endpoint backup and data protection solution is like investing in a “Kidnap and Ransom (K&R)” insurance – popular in the real world.”

